Spear Phishing in the Digital Ocean
Typically scammers cast a wide net for their phishing campaigns in the hopes that someone from the random group will take the bate. But are you familiar with spear phishing and how it’s different? Take a look at this scenario to spot the difference.
What would you do in this situation?
Spear phishing targets specific individuals or companies. One of the most common examples is BEC, or business email compromise. BEC attacks come in many different shapes and sizes. Here’s one example:
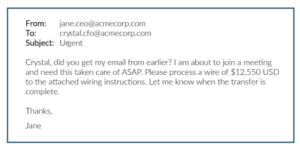
What’s Crystal supposed to do in this situation? Her boss is asking her to take care of something important ASAP. She might not want to bother Jane if she’s in a meeting. And the email itself doesn’t look threatening. It comes from her boss, it uses clear language, and it addresses Crystal by name. What would you do?
The answer is call Jane.
Even if there’s a small chance that this is a legit email, you’d be much better off interrupting a meeting, or putting off the wire transfer until Jane is available, rather than complying with the request.
As always, treat all requests for personal information or financial transfers with a heavy dose of skepticism. And report all phishing emails ASAP! If you’re not sure how, please ask.













