Do you know the sender of every message you receive?
“I won’t fall for a phishing email.”
“The emails look so fake!”
“We have spam filters to catch things like that.”
No one thinks they are going to be a target of a phishing scam. And if they do receive a phishing email, they believe they’ll recognize it as fake. The truth is we all receive hundreds, or even thousands, of messages per day through email, text, phone, and social networks. It is highly unlikely that we recognize everyone who sends these messages. And that’s where social engineering comes into play. The technique consists of tricking targets (you & me!) by pretending to be trusted people or companies to convince users to share valuable data without even thinking twice about it.
Cunat, Inc., a local developer and property management company, felt the same way. They recognized that phishing was a viable threat but didn’t think simulated phishing testing was necessary. That changed after a member of their management team clicked on what appeared to be a credible email and entered their network domain credentials. After noticing a couple of spelling errors on the linked website, the manager sounded the alarm by contacting their Eder Casella Technology IT support team. We jumped into action reviewing the email and updating the network password. These same credentials were used in several other locations that also needed to be updated and checked immediately. The speed in which Cunat acted to initiate our monitoring capabilities saved them from further damage by these attackers.

Cunat then realized the value and asked us to roll out our simulated phishing testing and training to all their employees, including:
- An initial campaign test that sends 3 medium difficulty messages to each of their email accounts within a month period
- Quarterly phishing emails sent randomly to staff with varying difficulty
- Training videos for staff that have clicked on a simulated phishing campaign
- Customized manager training
- Yearly on-site cybersecurity training with all employees
- Full reporting on the campaign findings
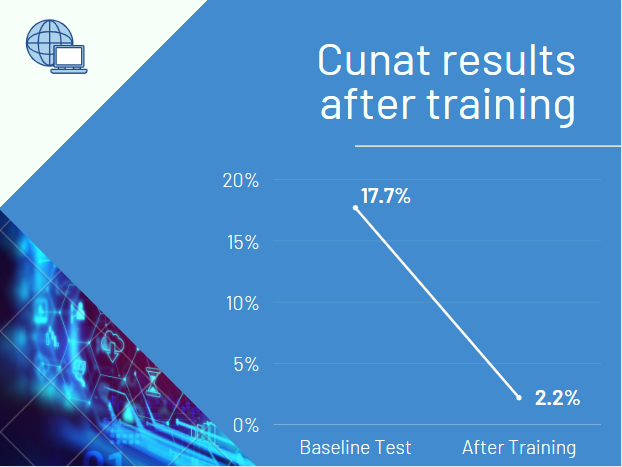
The results were almost immediate. During the initial baseline test, Cunat employees engaged with a simulated phishing campaign at a click rate of 17.7%. After on-site training and supplemental education for those that initially engaged, the click rate in the following quarter was down to 2.2%!
Education and training go a long way in securing your personal and company data. We’d welcome the opportunity to meet with you to discuss how Eder Casella Technology can help you to educate your team and protect you from future threats.







